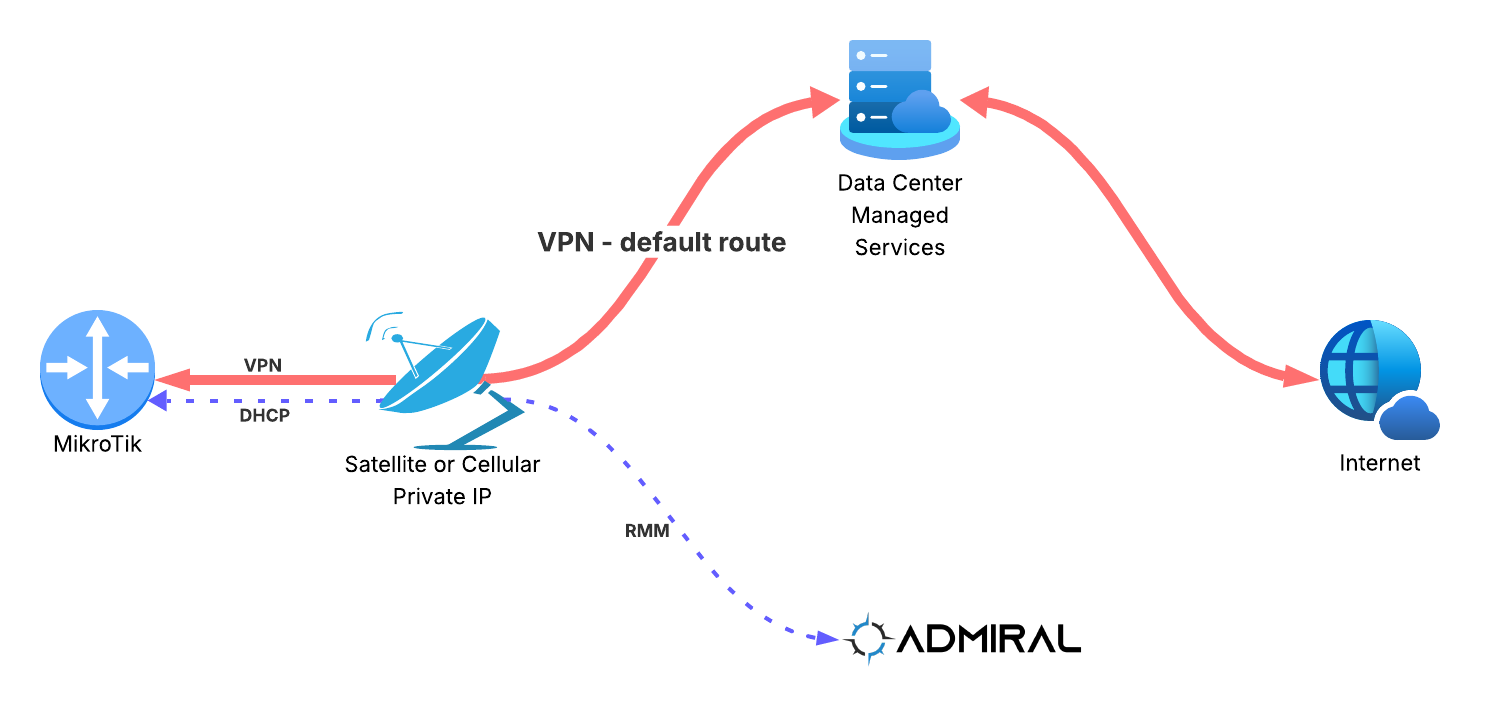
Recently we helped a new Admiral customer onboard a MikroTik that is configured to send…

RemoteWinBox security overview.
We’ve had a few questions recently regarding the security of RemoteWinbox and we thought we should make a blog post and FAQ to to help explain how we’ve approached security for our service and users.
- Firewalls for servers
- Only ports that need to be open to enable our service are accessible over the Internet
- Firewalls for routers
- Only the 1 single port assigned to a customer router is exposed/open for each router in your account and further…
- Access/allow list per company
- We track all of the IPs your company uses with our service to access your routers so that only the IPs you have used in our web GUI are allowed to get access to your gear. In other words, combined with above only your allowed IPs for your company can hit the pinhole firewall allowed ports
- Unique randomized credentials per Tik
- Anyone who managed to break into one Tik by using brute forcing our randomly generated credentials would not have access to any other Tiks with those same credentials
- Randomized port per router
- Even we have no idea what the next router will get assigned as the connection port that a new firewall hole will open up with. Combined with the access list that only allows members of your company to connect to your routers’ firewall pinholes, no one can reach your routers through our service, except from devices in your IP allow list!
- Secure communication channel
- We establish an end to end SSTP highly encrypted VPN tunnel so that no one can snoop your Winbox usage between our concentrator and your router