Different routers have different feature sets and management interfaces, though security remains paramount. Brute Force…
Admiral BOGON Process Explained
First, what is a bogon address?
In short, a bogon is an invalid address for passing traffic on the global Internet. They’re often used by bad guys to start malicious flows or by good guys on private networks.
From the APNIC website: “Bogon” is an informal name for an IP packet on the public Internet that claims to be from an area of the IP address space reserved, but not yet allocated or delegated by the Internet Assigned Numbers Authority (IANA) or a delegated Regional Internet Registry (RIR). The areas of unallocated address space are called “bogon space”. Many ISPs and end-user firewalls filter and block bogons, because they have no legitimate use, and usually are the result of accidental or malicious misconfiguration. Bogons can be filtered by using router ACLs, or by BGP blackholing.
So, a BOGON should NEVER appear in the global routing table. That being said, there are times you might be using a bogon.
Does filtering bogons matter?
Team Cymru CEO, Rob Thomas, studied a frequently attacked website to discover that 60% of the bad packets were obvious bogons (e.g. 127.1.2.3, 0.5.4.3, etc.). Your mileage may vary, and you may opt to filter more conservatively or more liberally. As always, you must KNOW YOUR NETWORK to understand the effects of such filtering.
Bogon filtering is a component of anti-spoofing filtering. Internet security includes an obligation to be a good steward of those resources under our care. If one sizeable network is insecure, it WILL be used to abuse other networks.
What’s the problem with filtering?
Well, many times you might use RFC1918 or RFC6598 reserved addresses to deliver packets from one spot on your network to another spot. That can happen without the traffic hitting the Internet, and this is a totally legit use case for these reserved addresses that are in the 192.168.0.0/16, 172.16.0.0/12, 100.64.0.0/10 and 10.0.0.0/8 ranges.
Because using some of these addresses is legitimate, Admiral attempts to perform a safe-mode of deployment that auto-discovers in-use bogons and excludes them from being filtered. Most of the time, this works great!
However, if you’ve tried to use the Admiral BOGON filtering and found that it looks like it applies, but then 5 minutes later the router removes the blocking rules, it’s probably because you’re using some bogons to get traffic around your network and the Admiral service is actually depending on the bogon traffic flow. Let’s explain…
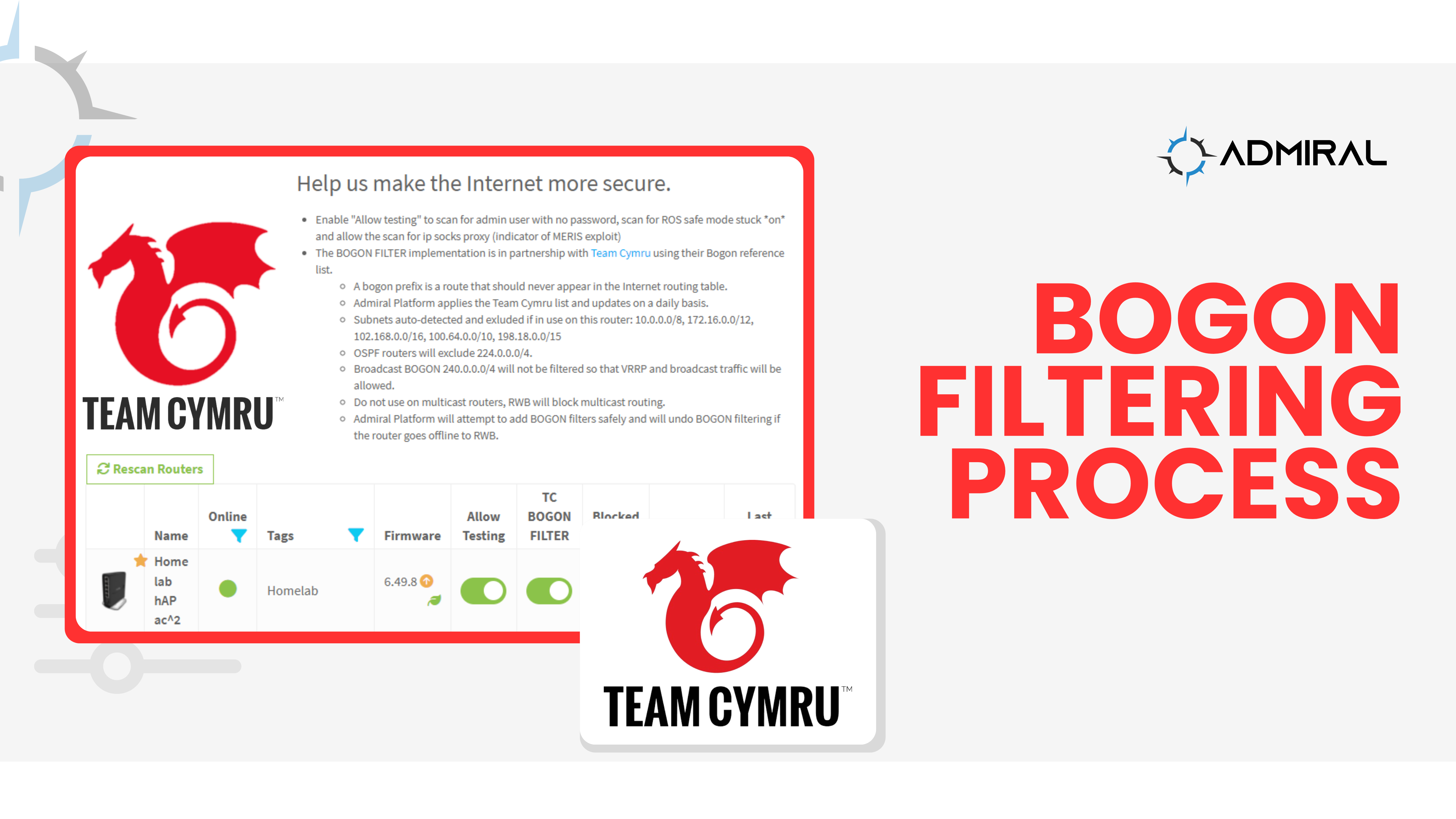
Here’s what happens when you click the BOGON filter in Admiral
- We add a schedule to prevent locking access out for this router that will get removed at the end
- Query the router for all IP addresses so that we won’t block reserved IPs this router uses
- Skip any BOGON prefix that is used in (2) (and skip broadcast subnet)
- Apply the rest of the BOGONs not skipped
- Add the firewall at the top of filters that references the BOGON list
- Block sourced and destined BOGON in all chains: INPUT, OUTPUT and FORWARD
- Trigger a discovery for this router
- If discovery is successful, the router must still be connected so unset the safe schedule from (1)
- else discovery failed, the router went offline and is probably using bogons, so allow the scheduler to finish to remove the firewall rules and will disable BOGON filtering
You can see that step 2 looks at the router configuration, so if enabling BOGON filtering is blocking your forwarding traffic for 10.x.x.x, 172.x.x.x, or 192.168.x.x what you can do is create a loopback (bridge) and assign a /32 IP to it and our BOGON filtering will ignore blocking of that subnet – the same can be accomplished for CGNAT (100.x.x.x).
How can I help Admiral detect BOGONS I’m using?
This does take a little bit of user intervention, but our system will auto-detect interfaces with IP addresses that are using BOGONS and will not block those reserved prefixes. So you can create a loopback (or bridge) interface and as an example of how to prevent Admiral from picking up any of the RFC1918 or RFC6598 space, you can copy + paste the following onto your Tik to ensure we don’t block any FORWARD traffic you’re using bogons for:
/interface bridge add name=loopback10
/interface bridge add name=loopback172
/interface bridge add name=loopback192
/interface bridge add name=loopback100
/ip address add address=10.99.99.99/32 interface=loopback10
/ip address add address=172.31.99.99/32 interface=loopback172
/ip address add address=192.168.99.99/32 interface=loopback192
/ip address add address=100.64.99.99/32 interface=loopback100
I’ve put in some 99s in there, feel free to adjust those to an address that won’t interfere with your network operation.
Feel free to save the above as a Fleet Commander job and then you can launch it anytime to prepare your router for worry free BOGON filtering!