https://www.youtube.com/watch?v=TiKrWahs5pY Bridge Mode is where we get real with real-world operators—no vendor fluff, no theory-only…
Brute Force Login Protection Tips
4.
Brute Force Login Protection Tips
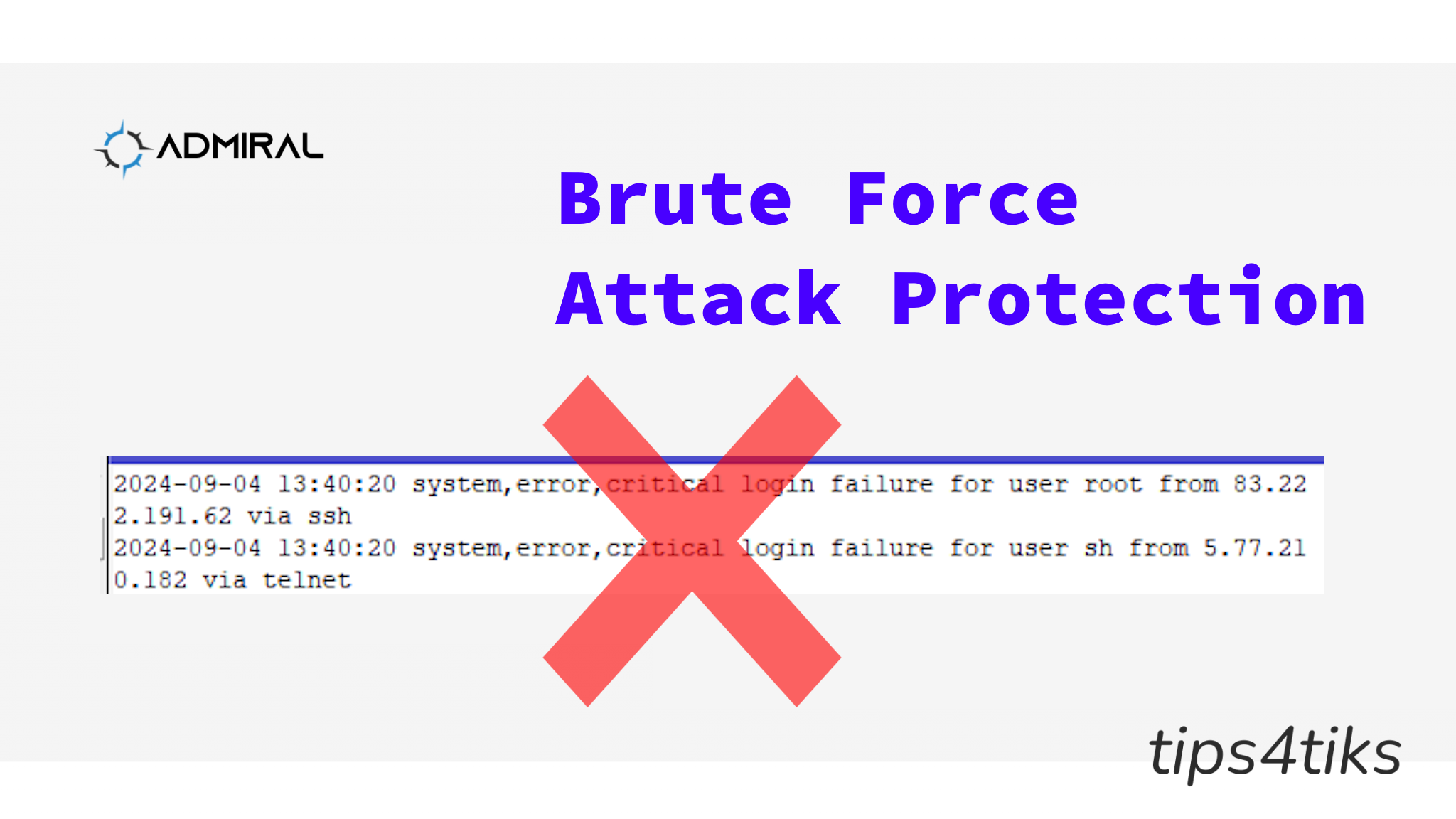
Every public IP address is vulnerable to attacks. One of the most common attacks is the SSH brute force attacks, a hacking technique where automated tools try thousands of different usernames and passwords in an attempt to gain access. Defense against SSH brute force attacks needs to be multi-layered, including using strong login names, passwords and firewalls.
MikroTik offers firewall settings for many strategies to defend against brute force attacks. Do be aware when setting up your method to not block yourself in the process! Few things are more embarrassing than getting locked out accidentally and needing to fix a router in person. Trusted lists can be created using Firewall Address Lists under the command: /ip firewall address-list.
Packets can be matched against a list to allow or block specific IP addresses. Creating a Trusted list first before adding any other firewall rules is strongly recommended. This list should likely include yourself, private network addresses, or commonly used VPNs. You can add a firewall input rule at the top of your list to allow Trusted addresses. You can also add Trusted based on in-interface, in-interface-lists, MAC addresses, and more.
Disabling Telnet is an additional defense option, which can be done readily on a MikroTik router with /ip services disable telnet.
The MikroTik wiki (https://wiki.mikrotik.com/wiki/Bruteforce_login_prevention) offers one method for limiting login attempts to protect against brute force attacks. Once you have your Trusted list, to avoid locking yourself out, you can set a number of login attempts before an IP address is blocked on a specific port.
Notably, this would only affect attacks tied to those ports. Another strategy is to treat each connection type as new so each syn syn/ack ack will be a flow in TCP. Then this would not be reliant upon which dst-port they try. This way, a firewall rule can catch attempts regardless of protocol based on the high traffic flow, such as no more than 100 new flows a minute from a new connection.
IP Firewall Raw is very useful for mitigating attacks by bypassing or dropping packets before connection tracking. (https://wiki.mikrotik.com/wiki/Manual:IP/Firewall/Raw). As an example of using Firewall Raw and Firewall rules in combination to limit based on more than 100 new flows per second:
/ip firewall raw
add action=jump chain=prerouting comment="If you hit the WAN with more than 100PPS and are not TRUSTED, jump to too_many_pps" dst-limit=100,5,src-address/1m40s in-interface-list=WAN jump-target=\too_many_pps src-address-list=!TRUSTED
add action=add-src-to-address-list address-list=BLOCK address-list-timeout=1d chain=too_many_ppsAdd these rules to the firewall filter relatively high on the list, though still under your Trusted rules:
/ip firewall filter add action=tarpit chain=input comment=“TARPIT BADS” protocol=tcp src-address-list=BLOCK
/ip firewall filter add action=drop chain=input comment=“BLOCK BADS” src-address-list=BLOCK These rules took a router from this:
To this long BLOCKED list:
Mitigating attacks is crucial to any network, especially those with public facing IP addresses. No one is immune. Brute force attacks such as SSH can and will affect everyone. Do remember to keep your passwords and usernames strong as well as use firewall tools and monitor your logins!
Stay tuned for more tips4tiks and happy networking!
We hope you find these posts as beneficial as we do. As always, we welcome your feedback and suggestions on how we can continue to improve the content we share. Visit our YouTube Channel for more tutorials and education content.